-
About
- About Listly
- Community & Support
- Howto
- Chrome Extension
- Bookmarklet
- WordPress Plugin
- Listly Premium
- Privacy
- Terms
- DMCA Copyright
- © 2010-2025 Boomy Labs


 Sandra Bauman
Sandra Bauman
Listly by Sandra Bauman
These are resources on the topic of data breaches and data security and their impact on reputation.
Showing real concern for those impacted is important, however. "Communicate that you take such incidents seriously. Describe efforts that you and your organization are taking to fix the situation," she urges. Also, Hodge advises not to give too much detail regarding measures the organization takes to protect against future breaches, as that might put the electronic data in even further trouble.
On April 20, 2015, the Securities and Exchange Commission ("SEC") issued a press release announcing an enforcement order (the " Order ") reflecting the settlement of charges against BlackRock Advisors LLC ("BlackRock" or the "Firm") and Bartholomew A. Battista, who had previously served as the Firm's Chief Compliance Officer ("CCO").

Not long ago, I was working on a speech and found myself trying to come up with a phrase that encapsulates the difference between organizations that really make cybersecurity a part of their culture and those that merely pay it lip service and do the bare minimum (think ' 15 pieces of flair ').

As in other policy areas where Obama has been unable to get legislation through the now Republican-controlled Congress, the White House is turning to more limited administrative actions to advance its agenda as much as it can. The announcement could be tonight or tomorrow, when the U.S.

In case any of you loyal readers missed it, KrebsOnSecurity.com and its author were featured in a 60 Minutes interview last night on the credit and debit card breaches that have hit countless retailers and consumers over the past year.

I've been thinking-and writing-a lot about privacy lately, and it's occurred to me that the term may actually be a misnomer when we're talking about the collection and use of data about individuals. Havens' voice is one in a growing chorus that contends the Internet economy in its current incarnation-specifically that of data in exchange for services-is fundamentally broken.

When Target lost data on some 110 million customers, it recommended them to credit bureau Experian for "identity theft protection," offering to cover the cost for a year. Think you're in better hands? Think again. Sometime before the Target hack, Experian had its own data leak -- via a subsidiary.

EMC recently identified the Privacy Paradox, indicating that consumers want all the benefits of technology, but "take virtually no special action to protect their privacy," despite an awareness of potential risks and security threats. What can explain this inconsistency? Essentially, humans are cognitively lazy. We know this from the Paradox of Choice.

More and more business value and personal information worldwide are rapidly migrating into digital form on open and globally interconnected technology platforms. As that happens, the risks from cyberattacks become increasingly daunting. Criminals pursue financial gain through fraud and identity theft; competitors steal intellectual property or disrupt business to grab advantage; "hacktivists" pierce online firewalls to make political statements.
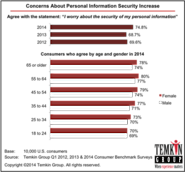
As part of Temkin Group's ongoing benchmark studies, we routinely ask consumers whether or not they agree with the statement, I worry about the security of my personal information. We found a significant jump in worried consumers in our most recent study, from 68.7% in Q1 2013 to 74.8% in Q1 2014.

Consumers trust marketers and advertisers with their data about as far as they can throw 'em. More than half of those participating in a recent privacy study said doctors, search engines and banks warrant their trust when it comes to personal data protection.

Even as the fallout from Target's holiday security breach continues -- the retailer's chief information officer resigned last week -- the brand is slowly returning to a normal marketing cadence. Shoppers visiting its stores are being prompted to sign up for the retailer's credit card.

Let us know if we missed any big data breaches. " Safely check if your details have been compromised in any recent data breaches: https://haveibeenpwned.com/ " See the data:bit.ly/bigdatabreaches This interactive 'Balloon Race' code is powered by our forthcoming VizSweet software - a set of high-end dataviz tools for generating interactive visualisations.

The following script is from "The Data Brokers" which aired on March 9, 2014. Steve Kroft is the correspondent. Graham Messick and Maria Gavrilovic, producers. Over the past six months or so, a huge amount of attention has been paid to government snooping, and the bulk collection and storage of vast amounts of raw data in the name of national security.

"Why are you doing this? We're a hospital. No one will want our data," was a comment Holly Meyers, RN, FACHE, then the senior vice president of quality, risk management, and insurance at Sylvania Franciscan Health frequently heard when she decided in late 2007 that carrying insurance to protect the seven-hospitals system in the event of a cyberattack or a data breach was a responsible choice.

From Combating Cybersecurity to the Threat of Online Privacy By: Jaime Neely - Published: Apr 18, 2014 * References: Internet safety is an issue felt at a micro and macro level. Individuals are constantly displaying hesitation in sharing personal information, whereas many governments are completely ill-equipped to protect their citizens.

Where is fraud and abuse enforcement headed in health care? One emerging area of interest is relationship scrutiny. Relationships can be complex in the business of health care: tracking and analyzing them is an important part of minimizing the fraud and abuse that may result from questionable relationships and improper influence.

The 'Internet of Things' could be a very good thing for cybercriminals, reports The Economist (7/18/15). In addition to the potential benefits to humanity, "smart devices offer exciting new opportunities for the authors of the malware that is common on today's Internet." The difference is that while "antivirus software may detect their handiwork and begin ...

What's your company's reputation worth? More than 300 business executives from around the world say a company's reputation is a priceless asset that should be protected as if it's a matter of life and death, because from a business and career perspective, that's exactly what it is.

Create a FREE account to: Get 15 free articles per month* Access to personalized content Save articles and create shareable folders in your personal HBR library Get 20% off your first order using code HBRORGREG3** not including articles that are exclusively for Harvard Business Review magazine subscribers *does not include

The majority of consumers (83%) are concerned about which businesses have access to their data and whether it’s safe, according to the findings of a government report.

With the holiday season upon us, much attention turns to the retail sector, which is expected to see unprecedented activity as shoppers in a strengthening economy take advantage of seasonal deals and yet-further-expanded shopping hours. However, overshadowing the energy of the holiday shopping season, the specter of data breaches past sits more and more heavily on the minds of consumers and companies alike. As they whip out their credit cards and swipe their debit cards at millions of POS terminals this November, will the data on those cards be secure, or will they get their post-holiday statement to find mysterious charges and unfamiliar purchases?

This is the text version of a talk I gave on September 14, 2015, at the FREMTIDENS INTERNET conference in Copenhagen, Denmark.

Hollywood Presbyterian Medical Center can have its computers back for $3.6 million in bitcoin.
