-
About
- About Listly
- Community & Support
- Howto
- Chrome Extension
- Bookmarklet
- WordPress Plugin
- Listly Premium
- Privacy
- Terms
- DMCA Copyright
- © 2010-2025 Boomy Labs


 Valerio Anema
Valerio Anema
Listly by Valerio Anema
Dyman & Associates Risk Management Projects is a Risk Management firm whose main office is based in Boston, MA. We operate in the following fields: Cyber Security, Project Management, Emergency Management, Technology Governance, and Physical Security. Our company is a minority-owned enterprise with both MBE & DBE certifications http://dymanassociatesprojects.com/.
By Roger Bjork I recently attended the Healthcare Innovation Challenge where I met some customers and took a look at various healthcare IT challenges and innovations. I came away with a couple of strong impressions about the role of mobility in healthcare, in addition to some best practices for healthcare companies to follow.

Manufacturers of Industrial Oil Burners, Gas Burners, Burners Spares, Air Regulating Unit, Solenoid Assembly, Flame Sensors, Oil Spray Nozzles, Burners Accessories, Burners Controllers, Mumbai, India

Manufacturers of Industrial Oil Burners, Gas Burners, Burners Spares, Air Regulating Unit, Solenoid Assembly, Flame Sensors, Oil Spray Nozzles, Burners Accessories, Burners Controllers, Mumbai, India
Manufacturers of Industrial Oil Burners, Gas Burners, Burners Spares, Air Regulating Unit, Solenoid Assembly, Flame Sensors, Oil Spray Nozzles, Burners Accessories, Burners Controllers, Mumbai, India

Manufacturers of Industrial Oil Burners, Gas Burners, Burners Spares, Air Regulating Unit, Solenoid Assembly, Flame Sensors, Oil Spray Nozzles, Burners Accessories, Burners Controllers, Mumbai, India

Parks Associates is an internationally recognized market research and consulting company specializing in emerging consumer technology products and services. Since 1986, we have provided research and analysis to companies ranging from Fortune 500 to small start-ups through market reports, primary studies, consumer research, custom research, consultation, workshops, executive conferences, and annual service subscriptions.

Tricia Parks, Chairman, Founder, and CEO of Parks Associates, was recently recognized by Women in CE as a 2014 Legacy Awards honoree.
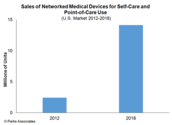
Networked Medical Devices to exceed 14 million unit sales in 2018 Firm sees Health Data Gateway as Strategic Investment Focus for device makers, care providers New digital health research from Parks Associates predicts U.S. unit sales of networked medical devices will exceed 14 million units by 2018, more than five times the sales from 2012.

Developing a Project Management program for your company can be a messy thing without the help of an experienced and well-trained consulting company with years of track record on the matter. Dyman’s approach allows your “project and program managers to adjust to and incorporate overall, departmental or specific project goals while keeping standardized levels of performance consistent with company-wide objectives.”

Watches, bracelets, gloves and hats, are currently being updated with Bluetooth wireless technology; which allows them to collect data and send it back to a smartphone or tablet application.

Bitcoin is a currency forged through hardcore mathematics and buoyed by promises of financial liberation from banks. Its climb has been very thrilling. Many are embracing bitcoin as a viable means of exchange and a valuable investment and it is rapidly increasing.

The unsuspecting and unwary Facebook users are being lured by cybercriminals with the promises of shiny gadgets. These scammers took advantage of the time when everyone is looking out for last minute deals ahead of Christmas.
[Are you getting the most out of your security data? See Dyman & Associates Risk Management Projects blog updates(http://dymanassociatesprojects.com/blog/) for techniques and security trends.]
To read more about Risk Management Projects articles, visit our website @ http://dymanassociatesprojects.com/.

Risk Management Key to Successful Volunteer Program
The Federal Government’s plans to expand the work-for-the-dole scheme promise plenty of debate about volunteer rights and responsibilities.
Risk management not only reduces potential liabilities and reputational harm, it also demonstrates the desire to create a safe environment and protect the wellbeing of volunteers, staff and service recipients.
It’s recommended that all tasks that pose hazards should be carried out by trained staff or contracted professionals. Learn About Cyber Security
Want More? Visit Our Website Dyman & Associates Risk Management Projects

Climate change is fundamentally a risk management problem. Whether or not you agree with the 97 percent expert consensus on human-caused global warming, there is an undeniable risk that the consensus is correct and that we're causing dangerously rapid climate change. Frequently, climate contrarians argue against taking action to mitigate that risk by claiming the uncertainties are too large.
Its remarkable how much can change over the course of just a couple of years. We've seen bring-your-own-device (BYOD) evolve from a buzzword to an accepted practice with a strong business use case. Cyber criminals are savvier than ever and using mobile-optimized techniques and malware to obtain more targeted prizes, such as Social Security numbers and credit card information. Decade-old attacks are even resurfacing under new guises, and with far greater precision than their predecessors. And of course, the proliferation of mobile devices available to an increasingly remote workforce continues to plague IT security professionals who are all too aware of the potential threats.
Unpredictability justifies the need for project management. How we prepare for the unpredictable is at the heart of enhancing project implementation — executing projects both in a rapid manner and with superior dependability on the committed targeted dates of delivery.
(Reuters) - The U.S. and UK governments on Monday advised computer users to consider using alternatives to Microsoft Corp's Internet Explorer browser until the company fixes a security flaw that hackers used to launch attacks.
The Internet Explorer bug, disclosed over the weekend, is the first high-profile computer threat to emerge since Microsoft stopped providing security updates for Windows XP earlier this month. That means PCs running the 13-year-old operating system will remain unprotected, even after Microsoft releases updates to defend against it.
(computerweekly) - Global IT association ISACA has launched its Cybersecurity Nexus (CSX) programme to help address the global security skills shortage.
According to the Cisco 2014 Annual Security Report, more than one million positions for security professionals remain unfilled around the world.
CSX is aimed at helping IT professionals with security-related responsibilities to “skill up” and providing support through research, guidance and mentoring.
(Japantimes) - With China a suspected source of cyberattacks, Prime Minister Shinzo Abe and European Union leaders will agree at a summit in Brussels on May 7 to launch a dialogue to boost cybersecurity, according to a draft of a statement to be issued after the meeting. "Facing more severe, widespread and globalized risks surrounding cyberspace .
See more:
http://dymanassociatesprojects.com/
https://foursquare.com/v/dyman--associates-projects/528dbcab498eeba21a51bf91
Cybersecurity insurance transfers some of the financial risk of a security breach to the insurer. But it doesn’t do a good job of covering the reputation damage and business downturn that can be triggered by a security breach.
See more:
http://dymanassociatesprojects.com/
https://plus.google.com/b/103237330230122996179/103237330230122996179/posts
http://dymanassociates.livejournal.com/
One of the most difficult challenges of cybersecurity is that it enables private actors to play a significant role in international security. Both security officials and international relations scholars tend to assume that states are the most important security actors.
As fresh graduates descend from the ivory tower (bearing their unstained diplomas), many will eventually encounter "real world" interactions for the very first time, and they run the risk of being eaten alive out there. Identity-connected scams, dark schemes and credit status traps litter the way to financial success.
Du ville ikke ønsker at flyve på et fly, der ikke har haft sin regelmæssige sikkerhed inspektion. Eller tage en tur uden at kontrollere din olie og dæk inflation. Eller gå glip af en årlig tur til lægen – ville du? På samme måde, med jævne mellemrum vurdere din IT-sikkerhed er en vigtig del af din organisations forebyggende vedligeholdelsesplan.
If your company has a Point of Sale (POS) terminal anywhere in its infrastructure, you are no doubt aware from the active media coverage that malware attacks have been plaguing POS systems across the country.
