-
About
- About Listly
- Community & Support
- Howto
- Chrome Extension
- Bookmarklet
- WordPress Plugin
- Listly Premium
- Privacy
- Terms
- DMCA Copyright
- © 2010-2025 Boomy Labs


Listly by personal-security-advice
The Internet is a great place to connect with friends and family, share ideas, and find information. But the Internet can also be an unsafe place.
Be cautious when sharing personal information online. Keep your computer's operating system and anti-virus software up to date
Use strong passwords, change them regularly. Do not open emails or attachments from unknown senders
Don't open suspicious email attachments or click on links within emails from unknown senders
Make sure online security threats don’t endanger your personal information

How Can You Protect Your Business?
It is virtually impossible to run a business today that doesn’t use electronic data and record keeping in some fashion. As a result, security risks are an unfortunate but a real threat for just about every business.

When you protect your website, you safeguard sensitive information and prevent damage to your business's reputation and financial security. Here's how to avoid cyber attacks. Even so, how do you deal with these attacks? Is there a way to safeguard your business and protect it from cyber-attacks? Read on for a detailed overview of what you can do to improve the security of your businesses’ online presence.

You create your website by putting in a great effort, but if you don’t have a strong security plan, everything can be lost in seconds. To save you from this, website security comes to your rescue. It saves your website data from hackers and cybercriminals who are continuously trying to exploit websites in one way or the other.

Backdoors can cause severe damage to your website. And you are very likely to suffer some or all of the following consequences.
• You lose potential customers by being redirected to a malicious site
• Mysterious popups on your web pages that asking visitors to download software
• Spam emails are being sent out from your Website / Domain Name
• Hackers can steal credit card information or medical records

We’ll share three ways through which backdoors are created. Then we will show you how to protect your computer from them. A backdoor is a method used to bypass security protocols and gain unauthorized access to systems. Hackers can use a backdoor to log in to your computer whenever they want to without you suspecting anything, thereby committing a backdoor attack.

A backdoor is a type of malicious software that gives a hacker access to your computer without your knowledge.
A backdoor on a computer is a type of malware that allows unauthorized access to your system. This can be done for many reasons, such as stealing data or installing other malicious software. Backdoors are often installed without the user’s knowledge and can be difficult to detect.
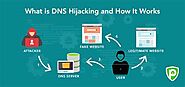
DNS is highly decentralized. No single DNS Server contains all the IP addresses and Domain Names for the whole Internet. Your request will travel across a multitude of DNS Servers before you see your results. DNS hijacking is the practice of redirecting DNS queries. You send out a query, but a third party steers the query the wrong way. As a result, a false IP address is used and the wrong website is shown in your Browser.

DNS hijacking cyberattacks manipulate transactions between servers and computers, leaving users unaware of what server they're using during an internet session. DNS redirection changes how a DNS transaction is handled by “hijacking” it, leading the user’s system to connect with a server that is not the intended destination on the internet. This malicious exploit takes the user’s traffic and then redirects it to a rogue DNS server.

Domain Name System (DNS) hijacking, sometimes called DNS redirection, is a type of cyberattack in which a user is redirected to a malicious site without their knowledge. Attackers execute DNS attacks by installing malware on a user’s computer or by hacking DNS communications.

In a DNS attack, DNS is compromised or used as a vector. Learn about attack types and how to prevent, detect, and mitigate them. A Domain Name System (DNS) attack is one in which a bad actor either tries to compromise a network’s DNS or takes advantage of its inherent attributes to conduct a broader attack. A well-orchestrated DNS attack can bring an organization to its knees.

HTTPS or SSL Security is not just for online stores anymore, the truth is all websites will benefit from being Secured. HTTPS protects the integrity. SSL sites ranking higher with Google. Provides Verified Proof of Identity'

Learn how to secure a website for free with SSL certificates, security training, free security tools, and more. Cybersecurity attacks and threats have grown in recent years, which makes securing your website all the more important. Security is even more critical for websites with online transactions, such as ecommerce websites, and for websites on widely popular platforms like WordPress.

Companies and organizations need to add SSL certificates to their websites to secure online transactions and keep customer information private and secure. In short: SSL keeps internet connections secure and prevents criminals from reading or modifying information transferred between two systems. When you see a padlock icon next to the URL in the address bar, that means SSL protects the website you are visiting

Fix SSL or HTTPS Warnings
SSL Certificate Problems
Explanation of SSL Certificate Errors
Mixed SSL Content Warning Error Examples
HTTPS warning normally indicates that both secured and unsecured elements are being served up on a page that should be encrypted
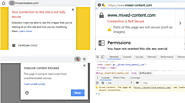
If you recently migrated your website from an insecure HTTP connection to a more secure HTTPS connection, you may still run into the problem of receiving mixed content warnings. Worse yet, your site may render as insecure to site visitors, causing them to quickly click the ‘back’ button and find elsewhere to explore.

Is your WordPress website displaying the ‘mixed content’ warning? Don’t panic. This warning can strike on any site even if you have installed a Secure Socket Layer (SSL) certificate. The mixed content warning does not stop your site from showing content on a page, but it can have a negative effect on your site’s SEO ranking. That’s why you should resolve it as soon as possible.

Websites unfortunately have a high degree of Security Risks. So are the Networks that the Servers connect to
With the growing dependency on the Internet today. Secure access to any website is becoming paramount. If you have any assets of value or if anything about your website puts you in the public spotlight. Then your website security WILL be tested.

Internet security is a broad term that refers to a wide range of tactics that aim to protect activities conducted over the internet. Implementing internet
As the internet expands and becomes an even bigger part of our lives, cyberthreats continue to grow both in scope and sophistication. These security threats come in different forms and vary in terms of complexity and detectability.

The safest method is to buy good internet security software, a program that will immediately remove viruses, advice you when you are browsing the internet and click on a malicious site and one that does regular scans of your computer to detect any damaging materials which may compromise both you and your computer.

You can control the traffic flowing into your Server. CFS's firewall can close connections and allow you to selectively open the connections from which you want to receive traffic.
Prevent DDoS attacks. A DDoS Attack is an attempt to make a Web Server or Website unavailable or to go down by overwhelming it with traffic from numerous sources.

Many of our Technical Support Analysts recommend that you use ConfigServer Security & Firewall (CSF), a free product that ConfigServer provides. CSF contains a stateful packet inspection (SPI) firewall, a login and intrusion detection mechanism, and a general security application for Linux servers.

ConfigServer Security & Firewall (csf) is one of the famous and advanced software firewall for Linux operating system. It is very famous and running on 1000000+ servers, that prevents unnecessary attacks. Especially csf is used in cPanel servers to prevents web based attacks, Brute-force attacks and DDOS. It is used as a Packet Inspection Firewall

How to Identify a DDoS Attack. The most common symptom of a DDoS attack is when a website, Server, or services suddenly becoming slow or unavailable. Keep in mind that a number of causes, such a legitimate spike in traffic, can create similar performance issues. Traffic analytics tools can help you spot some signs of a DDoS attack.
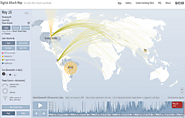
The IT industry has recently seen a steady increase of distributed denial of service (DDoS) attacks. Years ago, DDoS attacks were perceived as minor nuisances perpetrated by novice attackers who did it for fun and it was relatively easy to mitigate them. Unfortunately, that situation is no more. DDoS attacks are now a sophisticated activity, and in many cases, big business. InfoSecurity Magazine reported 2.9 million DDoS attacks in Q1 of 2021

A Denial-of-Service (DoS) attack is an attack meant to shut down a machine or network, making it inaccessible to its intended users. Victims of DoS attacks often target web servers of high-profile organizations such as banking, commerce, and media companies, or government and trade organizations. Though DoS attacks do not typically result in the theft or loss of significant information or other assets, they can cost the victim a great deal of time and money to handle.