-
About
- About Listly
- Community & Support
- Howto
- Chrome Extension
- Bookmarklet
- WordPress Plugin
- Listly Premium
- Privacy
- Terms
- DMCA Copyright
- © 2010-2025 Boomy Labs

 Fox Pass
Fox Pass
Listly by Fox Pass
Zero trust model is one of the best way to reduce the number of cyberattacks in the big organizations.

Zero trust model is a strategic initiative security system that helps to protect data by managing successful data breaches by reducing the concept of cyberattacks from an organization's network architecture. Zero trust is a great security system that helps to manage your data.

The zero trust model is a strategic network security system that helps prevent your critical data from data breaches.
Its policies are only for data security as it protects the surface by identifying the user's accounts and personal details.
Benefits of its policies are -
1) It has dual operating policies.
2) Zero trust divides duties in the system.
3) Data using limits based on your key employees.
4) Apply the least privileges.
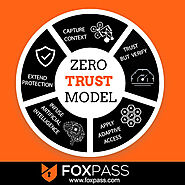
In an organization, users can face some challenges in implementing the framework of the zero trust model.
1) Legal:- Legal apps, network resources, authentication protocol, and administration tools are part of the network and your enterprise's operations.
2) Regulations: The Zero trust model does not support any regulation policies, which means the organization under compliance may have some trouble passing network audits.

A comprehensive workplace has a huge stock of critical data, which security is essential. The best security system gives highly configurable and strict protection to your sensitive data.
If you are confused about finding the right security system for your organization, then the zero trust model is the best choice for your business. Its implementation process is not too complex.
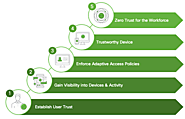
Yes, it is the latest and most secure network security system. These days, every organization uses the latest digital security system such as the zero trust model. It gives data using permission only to users who are working in the organization.
This is an advanced data security technology that gives highly configurable security to the users sensitive data from the data breaches and cyber attackers.

The new buzz in the cybersecurity system is the Zero Trust Model. With this modern approach, users' data will get safe network coverage, protection, and it becomes the first option for users & their data security.
The Zero Trust Model was developed in response to an increase in the number of data breaches caused by internal sources.

The zero trust model is a network security framework that gives strict security to the users’ personal or private data. If you want to implement this security system in your big organization, then you don’t need to be worried about unnecessary data transferring, using, or accessing. It gives data access permission for those users who can verify their identities.

A zero trust model is coordinated with cybersecurity and system management, which is based on recognizing the danger of theft present inside and outside in network boundaries. It helps store your sensitive data in the system database. It gives access only to users who have access to user data.

The Zero Trust Model is a cybersecurity strategy that secures current settings while also allowing for digital change. The "never trust" guideline is followed by this approach.
It uses robust authentication methods such as two-factor authentication or a physical token to lessen the danger of an online compromise.
