-
About
- About Listly
- Community & Support
- Howto
- Chrome Extension
- Bookmarklet
- WordPress Plugin
- Listly Premium
- Privacy
- Terms
- DMCA Copyright
- © 2010-2025 Boomy Labs

 John Gruber
John Gruber
Listly by John Gruber
Productivity and technology to make the world a better place. Because we all need a little help and motivation sometimes.

Microsoft Lists is a new app that is available with Microsoft 365. With Microsoft Lists, you can create a list to organize information. Store, share and collaborate with others in a clean list…
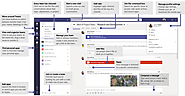
Microsoft Teams is a communication platform much like Slack that combines one on one & team chat, video meetings, and file storage. Teams also has a number of application integrations that can be…
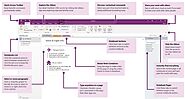
OneNote is a digital notebook that automatically backs up to Microsoft’s Office 365 cloud. Microsoft has developed apps for every device including Windows PC, Mac,iPhone, Android. OneNote notebooks…
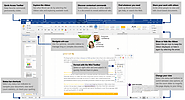
While working for Microsoft, Charles Simonyi and Richard Brodie developed the first version of Microsoft Word. The two developers chipped away at Xerox Bravo, the principal WYSIWYG (What You See Is…
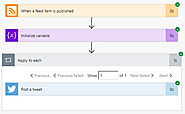
But why should marketing take half your time? Get it off your plate so you can focus on the more creative processes. I know what you’re thinking… Automatically posting a tweet when you publish a…
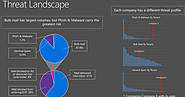
There’s a constant threat to your organization. Email is one of the most common ways hackers attempt to breach your organization’s security. Over half of the messages received are spam, phishing…

Everything you need to know about the anatomy of a great phishing email, with insights from a cybersecurity expert. We'll walk you through exactly what a ha...

This step-by-step guide will walk you through the process of configuring policies to prevent the use of outdated and auth protocols. Strengthen your security posture by ensuring only modern, secure authentication methods are used.

Ever clicked on a link in an email and wondered if it was really safe? That’s where the link scanner comes in. It’s like having a digital bodyguard for your emails, making sure you’re not walking into any traps set by cybercriminals.
