-
About
- About Listly
- Community & Support
- Howto
- Chrome Extension
- Bookmarklet
- WordPress Plugin
- Listly Premium
- Privacy
- Terms
- DMCA Copyright
- © 2010-2025 Boomy Labs


Listly by annachapman002
For all the cyber security Jedi's out there..here is a quick list on how automating your daily security tasks can benefit you:
Download this factsheet today to get a deeper insight into how a SOAR platform can streamline security processes.
DNIF brings you a variety of features to work with your data, here is a quick tutorial on how to get started with DNIF

Next Generation Security Analysts
Other benefits:
Discover quickly — DNIF identifies and provides accurate, real-time information about your endpoints regardless of operating system, location or connectivity.
Monitor continuously — Enable continuous monitoring and compliance enforcement across endpoints.
Create Baselines — Establish a baseline of normal endpoint and user activities and continuously monitor ongoing endpoint and user behaviors against that baseline to identify abnormalities and the need for follow-up or remediation.
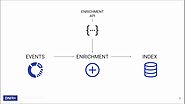
Enrichment = Enrich the data which is ingested to add/gain insight from the data. Example, the existing data about web authentication can be coupled with HR data to understand which user browsing patterns and sentiments.
Validation = If there seems to be a malicious activity from a know malicious IP addresses, cross check this IP address with Virustotal or Kaspersky if it has a bad reputation.
Response = You can directly issue a block request for an ip or a URL for most devices like your firewall or router :-)
Automation - Security automation is the automatic handling of a task in a machine-based security application that would otherwise be done manually by a cybersecurity professional.
Orchestration - Security orchestration is the connecting and integrating of various security applications and processes together.