-
About
- About Listly
- Community & Support
- Howto
- Chrome Extension
- Bookmarklet
- WordPress Plugin
- Listly Premium
- Privacy
- Terms
- DMCA Copyright
- © 2010-2024 Boomy Labs


 Kimberly Manahan
Kimberly Manahan
Listly by Kimberly Manahan
Information Technology trends and tips

With how convenient these things are for hackers, the question now is no longer, “who” hacked it but “when” will they hack you?

Given that your servers must be consistently efficient and reliable, it is best to explore your options that will fit the needs of your business in the short and long run.

An internal IT audit that aims to make sure these infrastructures, policies, and operations are working well and are coherent with the company’s goals is necessary.

Organizations maintain an internal IT audit team to oversee the operational integrity of their IT systems, considering how vulnerable today's IT environment has become prone to attacks-not to mention the financial costs and other losses included as well.

Before you start getting suspicious about the people working for you, know that according to studies, 95% of these so-called potential threats are unintentional.

Companies belonging to different industries, rely heavily on technology when it comes to managing their growing databases. However, due to the knowledge, skills, and persistence of unauthorized individuals or activities done by internal employees, unwanted circumstances occur, such as the incident of a security breach.

Since machines, software, networks, applications, and sometimes, even people fail, it is critical for any business to have proper measures set by data recovery experts to get back up after occurrence of any potential IT disasters.

This is why choosing the right IT partner is crucial not only in helping you prevent a security breach from happening but also essential in managing mitigation once a breach happens.
Being at least a step ahead can minimize potential problems for your business later on.

The purpose of why you are looking for an IT solutions provider to partner with is because you know that they know better about keeping your data secure more than you do. So choose one that fits the bill.

This checklist does not only cover the roles and responsibilities of IT personnel but more importantly, should be known by all employees or team members that have access to critical and confidential data of the company.

At present, a lot of businesses have chosen to outsource most of their work to keep costs down. Commonly seen in the Information Technology (IT) sector, several companies have shifted their IT infrastructure to countries with cheaper bandwidth and lower labor costs.

Our constant exposure to the Internet has brought about issues with security as well as privacy. #Cyberattack

In today’s technological landscape, having a robust IT security system in place is no longer considered a luxury, rather a necessity. #ITSecurity #Outsourcing

Instead of being paranoid and fearful as to what degree a crime in each episode may be true, let’s put those IT security lessons from CSI to good use.

Should organizations rely on talent or technology to protect themselves and their customers?

Nothing can be more horrifying than finding out that hackers have intercepted you and your clients.

Any IT infrastructure requires a systematic implementation of security measures to avoid occurrences of possible threats.

Studies show that companies practicing strict security procedures and methods on their IT systems can reduce the cost by as much as $14 per incident.

Knowing the possible security trends that would arise this 2016 is crucial in efficiently addressing the different challenges and issues that the business may encounter to avoid breaches and reputational damages and maintain privacy and data integrity, among others.

These security threats are relatively small compared to what usually makes rounds on the Internet, with cyber hacks getting more aggressive and complicated, thus, harder to mitigate.
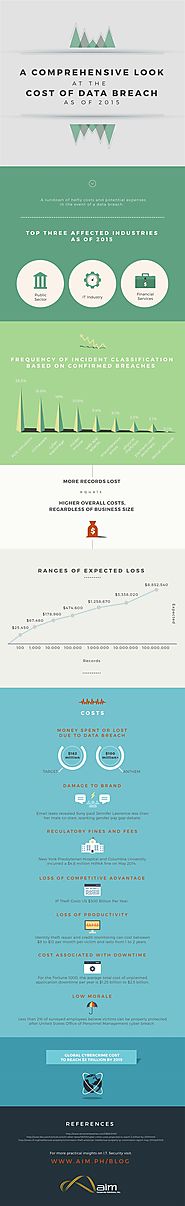
An infographic on the rundown of hefty costs and potential expenses on the event of an organizational data breach

There are several server and big iron keywords which have been lumped together simply because they sound alike. These include “high availability,” “mission critical,” and “fault tolerance.”

Unfortunately, there are still unhelpful habits that persist among leaders and managers since the beginning of the offshore outsourcing industry.
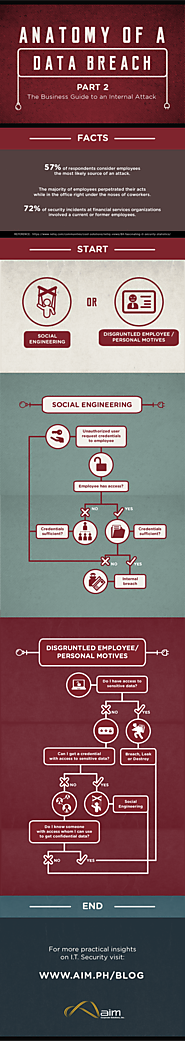
An infographic on how businesses can defend against data breaches
