-
About
- About Listly
- Community & Support
- Howto
- Chrome Extension
- Bookmarklet
- WordPress Plugin
- Listly Premium
- Privacy
- Terms
- DMCA Copyright
- © 2010-2024 Boomy Labs

 Shahid Sharif
Shahid Sharif
Listly by Shahid Sharif
All about protecting yourself on the internet

Last week, Arun Thampi, a programmer in Singapore, discovered that the mobile social network Path was surreptitiously copying address book information from users' iPhones without notifying them. David Morin, Path's voluble chief executive, quickly commented on Mr. Thampi's blog that Path's actions were an "industry best practice."

He leaves his cellphone and laptop at home and instead brings "loaner" devices, which he erases before he leaves the United States and wipes clean the minute he returns. In China, he disables Bluetooth and Wi-Fi, never lets his phone out of his sight and, in meetings, not only turns off his phone but also removes the battery, for fear his microphone could be turned on remotely.

Every day we hear news about the privacy concerns of social media. Nothing you do online is truly anonymous. Even proxy servers, which are made to mask your IP address, are easily traced when they need to be.

Dear Lifehacker, I understand that signing up for "free" services like Gmail and Facebook require that I put my trust in a company and provide them with quite a bit of personal data. I know that data is supposed to be kept private, but with the amount of information and web activity that's tracked every day I'm started to worry.

February 10, 2012, 2:35 PM - It's difficult to figure out where you stand in the eyes of the law these days TSA, the Dept.

Avivah Litan VP Distinguished Analyst 12 years at Gartner 30 years IT industry Avivah Litan is a Vice President and Distinguished Analyst in Gartner Research. Her area of expertise includes financial fraud, authentication, access management, identity proofing, identity theft, fraud detection and prevention applications…Read Full BioCoverage Areas: by Avivah Litan | February 13, 2012 | Submit a Comment Did I miss something?

Twitter Inc. has acknowledged that after mobile users tap the "Find friends" feature on its smartphone app, the company downloads users' entire address book, including names, email addresses and phone numbers, and keeps the data on its servers for 18 months.

By Cory Doctorow at 10:39 pm Tuesday, Feb 14 The Electronic Frontier Foundation's SSL Observatory is a research project that gathers and analyzes the cryptographic certificates used to secure Internet connections, systematically cataloging them and exposing their database for other scientists, researchers and cryptographers to consult.
As the Arab Spring hits its first anniversary, tech activists around the globe are continuing their efforts to enable secure communications-especially in areas of the world that are in conflict or transition.

Apple received a letter from Congress today, asking CEO Tim Cook to answers questions by Feb. 29 about how its app developers handle the privacy of iPhone users. It's in response to last week's news that Path, a social networking app, was caught by blogger Arun Thampi collecting address book [...]

February 14, 2012 12:35 PM ET Computerworld - The FBI today said that its proposed plans to monitor social media sites as part of a broader strategy to improve real-time situation awareness will be fully vetted by the agency's Privacy and Civil Liberties Unit.

A new bill that would require telecommunications providers to give police subscriber information without a warrant will likely be challenged in the courts if crucial changes aren't made, critics say. "A court challenge, I think will be inevitable, if this law passes as is," said University of Ottawa law professor Michael Geist, who holds a Canada Research Chair in internet and e-commerce law.

Over the weekend, Dave Winer wrote an article at Scripting.com explaining how Facebook keeps track of where you are on the web after logging in, without your consent. Nik Cubrilovic dug a little deeper, and discovered that Facebook can still track where you are, even if you log out.

There's been a lot of news lately about a lapse in either security or judgment -- both, really -- at Apple that allows iOS applications to borrow your contact data and send it off to parts unknown without your consent. Apple has addressed the issue to members of the U.S.

The raid that ravaged Megaupload was just the start. A powerful trade group that lists the biggest names in the entertainment biz as its members has called-out dozens of countries in their latest report and is insisting on sanctions against them.

Dark Reading is the premier online resource helping information security professionals manage the balance between protection and access. It offers breaking news and analysis on attacks, breaches and vulnerabilities, as well as strategies for protecting enterprise data. It also offers guidance on setting risk management and compliance policies.

Rep. Jackie Speier (D-California) said Thursday she wants the Department of Homeland Security to cease its social-media and news-monitoring operation.
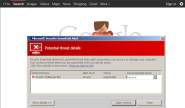
The world's most popular search engine was falsely identified by Microsoft as malware for four hours on Valentine's Day due to a faulty software security update, leaving many frustrated Internet Explorer users unable to access Google. The false positive affected searchers in the U.S., Middle East, Australia, New Zealand, and Denmark, according to ZDNet.

WASHINGTON - The FBI has begun cutting back GPS surveillance in an array of criminal and intelligence investigations following a Supreme Court ruling last month restricting its use, a federal law enforcement official said. The bureau began implementing the change the day after the Jan.

The Wall Street Journal reports that Google has been bypassing privacy settings in Safari intended to block websites from tracking user activity across the Internet. Stanford researcher Jonathan Mayer discovered that Google had been implementing code that bypasses Safari's user-determined privacy settings, and the Journal's own researcher independently confirmed Mayer's findings.
