-
About
- About Listly
- Community & Support
- Howto
- Chrome Extension
- Bookmarklet
- WordPress Plugin
- Listly Premium
- Privacy
- Terms
- DMCA Copyright
- © 2010-2024 Boomy Labs


Listly by cbeast0033
Strong cybersecurity measures are more important than ever in the rapidly changing digital world, when information is shared at the speed of light and cyber threats are everywhere. Encryption, a sophisticated but crucial technology that is at the vanguard of this digital defense, is crucial in protecting sensitive data from prying eyes. In order to demystify encryption, this essay will explain its significance, internal workings, and ways that it helps safeguard our digital environment.
At its core, encryption is a process of converting readable data, known as plaintext, into an unreadable format, referred to as ciphertext. The transformation is achieved through the use of algorithms and cryptographic keys, rendering the information indecipherable without the corresponding decryption key. The primary objective of encryption is to ensure the confidentiality, integrity, and authenticity of data during transmission and storage.
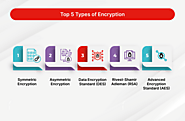
Symmetric Encryption:
In symmetric encryption, a single secret key is used for both encryption and decryption.
It is a fast and efficient method suitable for encrypting large volumes of data.
The challenge lies in securely distributing and managing the secret key.
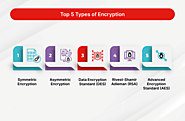
Asymmetric Encryption:
Asymmetric encryption employs a pair of keys – a public key for encryption and a private key for decryption.
Public keys are freely distributed, allowing anyone to encrypt data, but only the owner of the private key can decrypt it.
Asymmetric encryption is commonly used for secure communication and digital signatures.
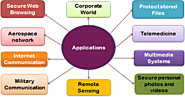
Encryption secures communication channels, ensuring that sensitive information exchanged between parties remains confidential.
Popular protocols like HTTPS use encryption to protect data transmitted over the internet.

Encrypted storage ensures that even if unauthorized individuals gain access to physical or digital storage devices, the data remains unreadable without the decryption key.