-
About
- About Listly
- Community & Support
- Howto
- Chrome Extension
- Bookmarklet
- WordPress Plugin
- Listly Premium
- Privacy
- Terms
- DMCA Copyright
- © 2010-2024 Boomy Labs


Listly by franzallan0033
In the ever-evolving digital landscape, events have undergone a significant transformation with the integration of technology. From virtual conferences to hybrid gatherings, the wealth of data generated during events has become invaluable for organizers and participants alike. However, with great data comes great responsibility, and ensuring the security of event data has become a paramount concern.

The digital era has brought about a plethora of opportunities but also challenges in ensuring the security of event data. Cyber threats, data breaches, and privacy concerns are ever-present risks that can compromise the integrity of sensitive information. Unauthorized access to participant details, financial data, or confidential discussions can have severe consequences, ranging from reputational damage to legal ramifications.

Event data encompasses a wide range of information, including attendee details, engagement metrics, feedback, and preferences. Organizers leverage this data to enhance future events, tailor experiences, and improve overall satisfaction.
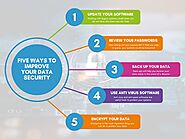
Encryption:
Implementing robust encryption protocols is fundamental to protecting event data. Encryption converts information into a code that can only be deciphered with the appropriate key, making it significantly harder for unauthorized parties to access sensitive data.

Secure Data Storage:
Choosing secure and reputable platforms for data storage is crucial. Cloud services with strong security measures, such as encryption in transit and at rest, can provide a reliable foundation for storing event data.

Establishing strict access controls ensures that only authorized personnel can access specific types of data. Role-based access can limit the exposure of sensitive information to only those who require it for their responsibilities.